Threat Watch
Instantly evaluate your cybersecurity health and get actionable insights to protect yourself now!.
Visit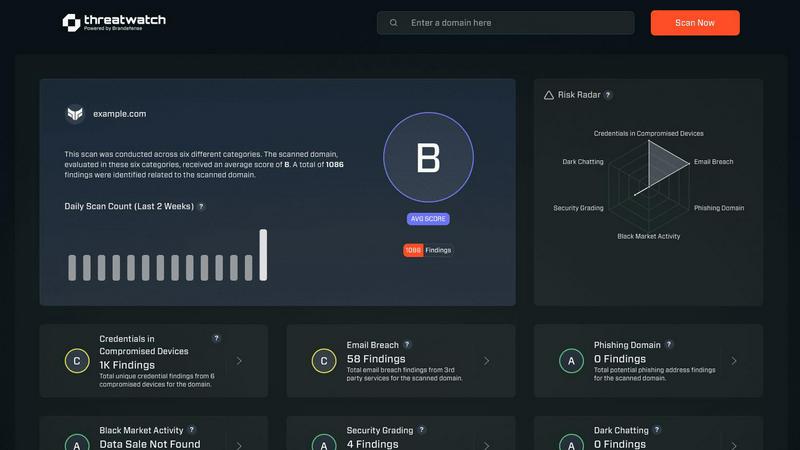
About Threat Watch
Uncover your Cyber Security Health, Fast! Threat Watch is your all-in-one cybersecurity intelligence command center, designed to give you unparalleled visibility into your organization's digital risk landscape! It's a powerful, unified solution that continuously analyzes your assets, vulnerabilities, and exposures across the clear, deep, and dark web to deliver a crystal-clear, real-time picture of your cyber health. This platform is built for IT leaders, security teams, and business executives who need to move from reactive panic to proactive control. By automating critical assessments and providing immediate insights, Threat Watch empowers you to identify hidden threats, prioritize the most critical risks, and take decisive action to mitigate them faster than ever before. Stop wondering about your security posture and start knowing with absolute confidence! Transform overwhelming data into an actionable security strategy today.
Features of Threat Watch
Comprehensive Cyber Health Scan
Jumpstart your security journey instantly with our powerful free scan! This feature delivers a rapid, high-level assessment across critical security categories, giving you an immediate snapshot of your most pressing risks. It's the perfect way to benchmark your current posture and identify glaring issues that need urgent attention, all within minutes!
Real-Time Threat Intelligence Dashboard
Gain a live, unified view of your entire threat landscape on a single, intuitive dashboard! This feature aggregates and correlates data on compromised devices, breached employee credentials, phishing-targeted email addresses, and dark web exposures. See your cyber health score update in real-time as new threats are discovered, keeping you always informed and ready to act!
Automated Exposure Monitoring
Set it and forget it! Threat Watch continuously and automatically scans the depths of the internet, including dark web markets and forums, for mentions of your company's assets. Get instant alerts if employee credentials are leaked, corporate data is traded, or your domains are spoofed for phishing campaigns, turning endless manual searches into efficient, automated protection.
Prioritized Risk Mitigation Guidance
Move from insight to action with clear, prioritized recommendations! Threat Watch doesn't just list problems; it analyzes the severity and context of each vulnerability and exposure to tell you exactly what to fix first. This actionable intelligence ensures your team spends time on the fixes that matter most, dramatically improving your security efficiency and effectiveness!
Use Cases of Threat Watch
Proactive Data Breach Prevention
Stop breaches before they start! By continuously monitoring for stolen employee credentials and corporate data on the dark web, Threat Watch enables your IT team to force password resets and secure accounts the moment a leak is detected. This proactive stance prevents attackers from ever using stolen data to access your systems!
Executive and Board Reporting
Communicate security status with powerful, easy-to-understand data! Security leaders can use the clear Cyber Health Score and visual dashboard from Threat Watch to demonstrate risk levels, justify security investments, and report on the effectiveness of current programs to executives and the board with compelling, factual evidence.
Third-Party and Supply Chain Risk Assessment
Extend your security visibility beyond your own walls! Use Threat Watch to evaluate the cyber health of your critical vendors and partners. By understanding their public exposures and credential leaks, you can assess the risk they pose to your own network and enforce stricter security requirements in contracts.
Rapid Post-Incident Investigation
Accelerate your response when a security incident occurs! If a phishing attack slips through or a device is compromised, Threat Watch's historical and real-time data provides crucial context. Quickly trace the source, see what other assets were exposed, and understand the full scope of the incident to contain damage and prevent recurrence faster!
Frequently Asked Questions
How does the free scan work?
The free scan is a quick, non-intrusive process that analyzes publicly available data and known breach repositories associated with your organization's domain. You simply enter your company's primary email domain, and our system scans for compromised credentials, exposed assets, and phishing risks, providing an immediate overview report without requiring any internal network access or complex setup!
What kind of threats does Threat Watch detect on the dark web?
Threat Watch actively monitors dark web forums, marketplaces, and chat channels for specific mentions of your organization. This includes stolen login credentials (emails and passwords), confidential corporate documents being traded, intellectual property for sale, and discussions about planning attacks like phishing or ransomware targeting your company. We alert you the moment your data appears!
Is Threat Watch suitable for small businesses?
Absolutely! Cybersecurity threats target businesses of all sizes, and small businesses are often prime targets. Threat Watch scales to fit any organization. The immediate insights from our tools, especially the free scan, provide a cost-effective way for smaller teams with limited resources to understand their major risks and take critical first steps toward improving their security posture without a massive upfront investment.
How often is my threat intelligence updated?
Your threat intelligence is updated in real-time! Our systems operate 24/7, continuously ingesting data from a vast array of global sources. The moment a new breach containing your data is published or a new discussion about your company is found on the dark web, your dashboard and alert systems are instantly updated to ensure you have the very latest information at your fingertips.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt revolutionizes contract management with fast, secure templates and seamless signing for effortless team collabo...
AILeadz
Unlock explosive growth with AILeadz, the ultimate tool that finds, verifies, and connects you with ideal customers!.